Choose the Platform for Device Management

Deploy and Manage Android Devices

Deploy and Manage Windows Devices
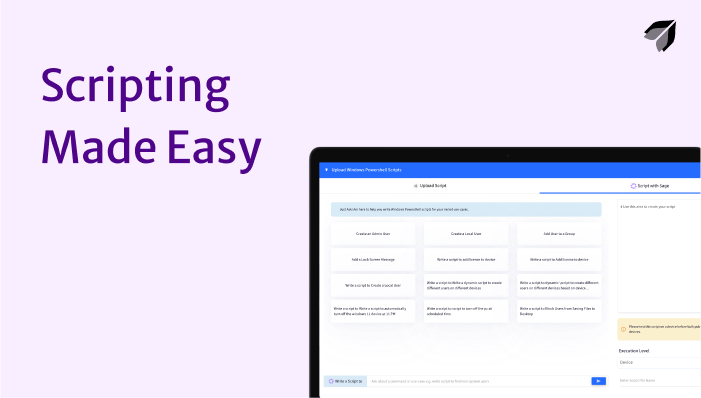
Explore our guides and examples to Scalefusion
Get Started with scalefusion DocumentationChoose the Platform for Device Management
Check out our video tutorials to understand and effectively utilize each feature of Scalefusion.



We provide an extensive collection of ebooks and guides, delivering expert insights to assist you in streamlining mobile device management, ensuring efficient device deployment, robust security, and enhanced productivity.
